The Underpants above Prague Castle (2015) project had an important episode that led to the creation of a separate follow-up “sub-project” called Decentralization of Power foregoing the important opening trial of the Criminal Court. It consisted of cutting off the flag of the President of the Republic taken from the roof of Prague Castle.
The flag had two sides (layers of the flag), which we marked -, +. We split it to 1152 pieces (both sides 24×24). It was one of the first ways to authenticate artwork on a blockchain. All the pieces had a public address on the website, but they were also recorded on the blockchain, so we could not create another piece of the artwork – not without reusing private keys, which could be detected. The addresses were funded with real Bitcoin.

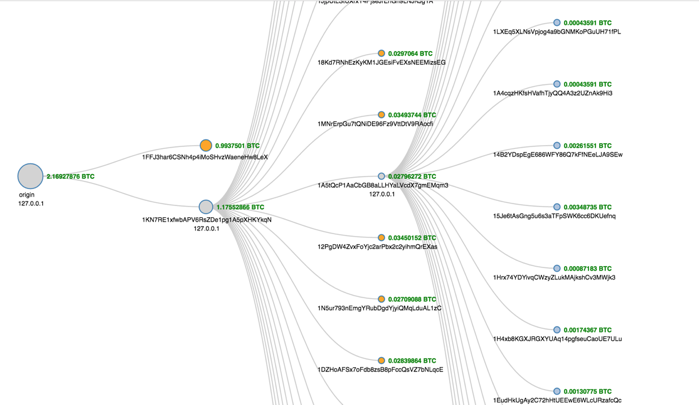
The structure was as follows: The initial coins were sent to 1zthvnV4gBun9HLt6aQxUzoJqPF8EP2SL . From there, there was a transaction sending it to two addresses, one for each side of the flag (- and +). Then there were 24 outputs and from each of them another 24 outputs, to identify a particular cut piece.
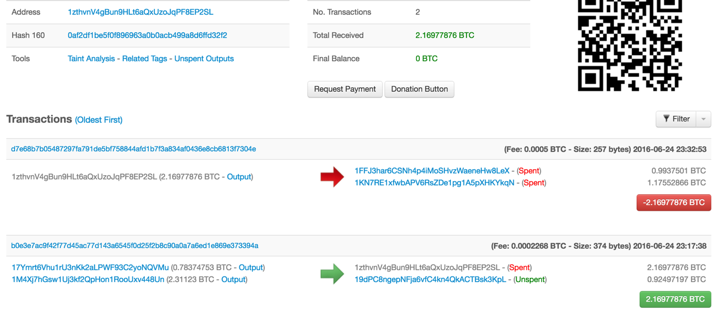
Anyone that could trace their public key to the initial transaction (which was permanently recorded in a Bitcoin blockchain) and had a matching private key that was not spent could verify that their artwork is an original and there were indeed only 1152 pieces of artwork created.
The addresses were generated from a master public key (also called „xpub“):
xpub661MyMwAqRbcGrauUKWQDx9dVvF5315xiT2AbxNrn5hF8gtrjAjtpYq7LmfyGFex1TjJWHihNtzDXVwCYSUy3LdfvbtuBDSADx4exncXSda
The derivation path was chosen as „m/side/x/y“. Side could be 0 or 1, x and y were both numbers from 0 to 23, generating 1152 addresses with corresponding private keys (for example +A1 was m/1/0/0, -B10 was m/0/1/9). We did not use hardened key derivation, which created a security vulnerability if both the xpub and at least one of the private keys were misused by an attacker.

These were converted to QR codes and printed on a particular piece of art put into envelopes, which were distributed to random people in 12 cities around the Czech Republic.

Presentation and xpub leak
By our mistake, the xpub key was published for a while at Ztohoven.com website. Despite the fact it was removed shorty, it was downloaded by Stick and Slush who exploited this vulnerability instead of disclosing and preventing any harm. They had multiple ways to notify us about the vulnerability according to responsible disclosure rules they are aware of as security and cryptocurrency professionals.
The given xpub key published online. Even if this was a case, a responsible reaction would be to disclose the vulnerability responsibly and do everything to limit the damage, not to quietly abuse it.
After they got the xpub key, they started to look for at least one piece of artwork with a private key – the xpub was useless unless they got their hands of at least one derived private key. Then deriving master private key and all other private keys is trivial. It was not a problem to do that since the artworks with wallets and covered QR codes were already publicly distributed.
We do not know how they got the private key exactly, but with the key and the xpub from the slides, they calculated the remaining private keys and sent the Bitcoin from all the addresses ( tx1 , tx2 , tx3 , tx4 ) that still had some balance to 1CUjWTJvfJrt4mgr79AB9Mj3zMt8hAp2iG . They included an OP_RETURN in the transaction with the text “spending transakce ze standarty: https://twitter.com/paralyzace_moci” which translates to “spending transaction from the standart” and links to the twitter profile of the project. At this time, we were informed by community members about the disappearance of bitcoins from the flag.
After we confronted them, they acknowledged that they have done it and insisted that this act is part of their art project. Only 18 people at that time withdrew their Bitcoin from the flag and were not victims of theft. In total 1.53535824 (plus transaction fees) Bitcoins were stolen from 1134 addresses.

No comments